DLL_Version_Enumeration_BOF
What is this?
What problem are you trying to solve?
How do I build this?
How do I use this?
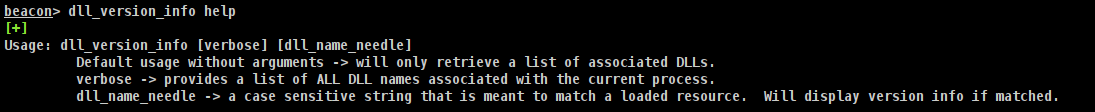
Any known downsides?
What does the output look like?
All known DLLs associated with the process
DLLs associated with the process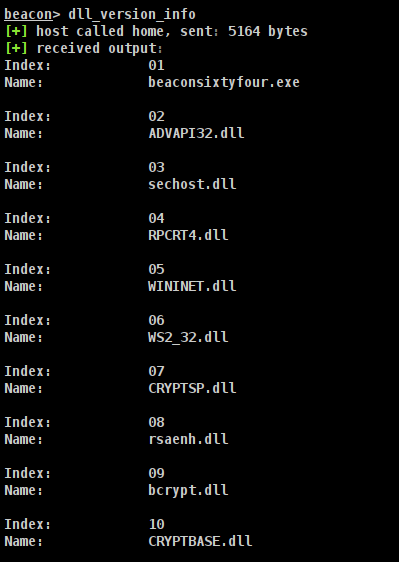
Verbose output of the aforementioned
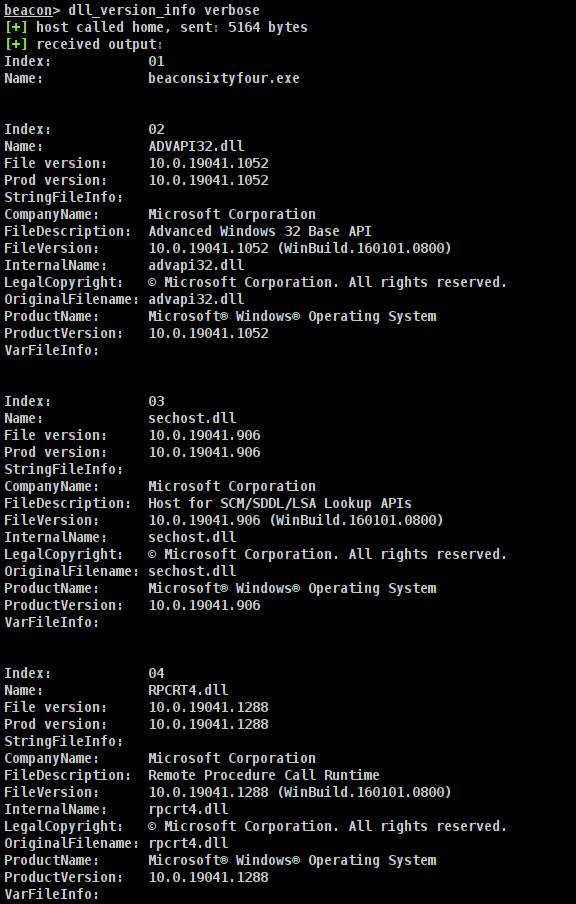
Verbose output of the aforementioned with needle
needle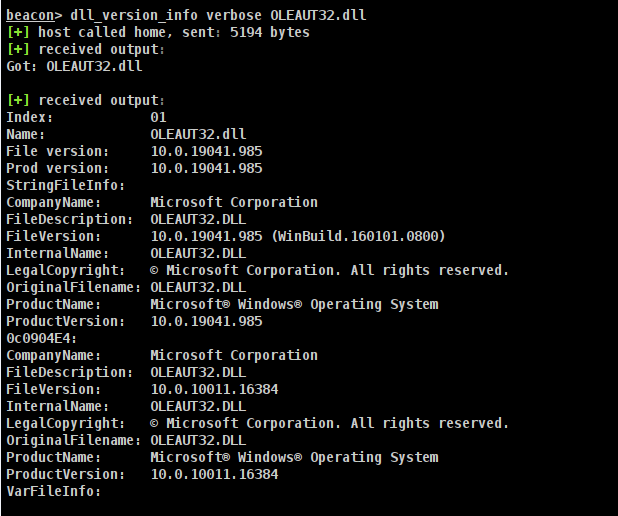
Last updated
